Cybersecurity expert Sami Laiho took the stage to deliver one of the most sobering yet insightful sessions of the CollabDays Finland 2025 conference. The talk covered everything from ransomware economics to AI impersonation, and painted a clear picture of the threats we face today—and tomorrow.
🔥 The Magic Numbers: 2 Hours vs. 180 Days
Sami opened with two critical statistics:
- 2 hours: The average time it takes for attackers to fully compromise a system after initial access.
- 180 days: The average dwell time attackers remain undetected in a system before launching their payload.
These numbers highlight the urgency of rapid patching, longer log retention, and proactive threat detection.
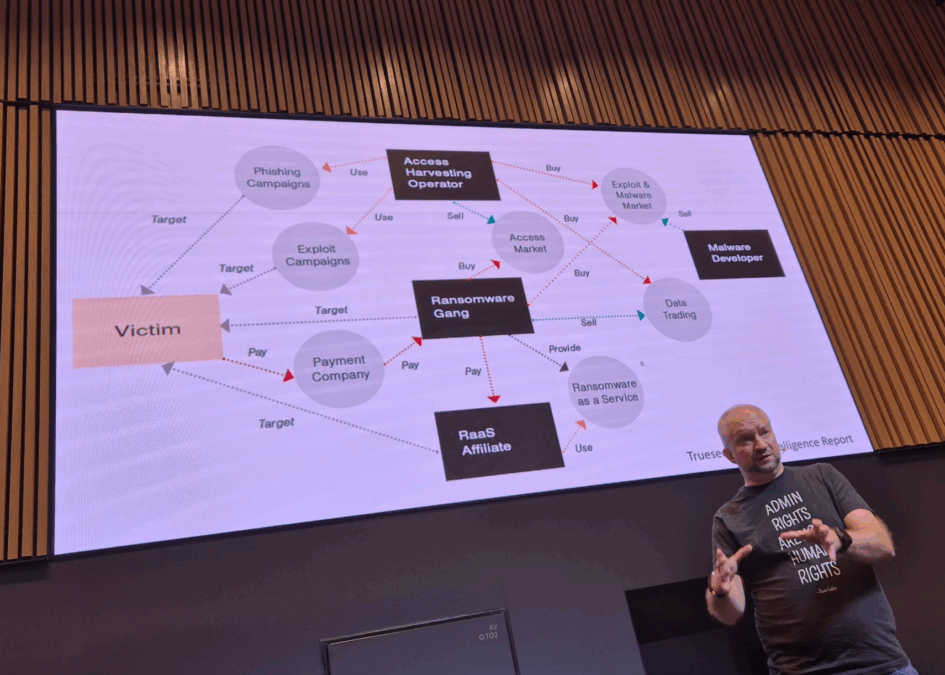
🧠 Ransomware Is Organized Crime
Forget the image of lone hackers in hoodies. Today’s ransomware gangs operate like mafia-style enterprises:
- They outsource tasks to affiliates.
- They run HR departments.
- They use outdated malware due to poor contract renewals.
- They target hospitals and manufacturers for maximum leverage.
A municipality in Finland was hit by LockBit 1, even though newer versions existed—because the attackers hadn’t updated their contracts.
🤖 AI Deepfakes: Identity Is the New Battleground
There was a live demo of an AI-generated deepfake. The fake Sami said things the real one would never say, in both Finnish and English.
“Everyone should login to Windows with Admin Rights” is a joke – that is the vulnerability – don’t log in with as admin
This wasn’t just a video—it was generated from a single image and voice sample, using free tools.
🏥 Why Hospitals and Manufacturers Are Prime Targets
Attackers now use Excel sheets to calculate how much money a company loses per day of downtime. Then they set the ransom just below that number.
- Hospitals: Public pressure forces quick payouts.
- Manufacturers: Easy to quantify losses, making them ideal targets.
“Some victims even asked for the Excel sheet—because they didn’t know how profitable they were,” Sami noted.
🧪 Patch More, Test Less
Sami’s mantra: “Patch more, test less.”
- Waiting two weeks for critical updates is too long.
- Attackers exploit unpatched systems faster than ever.
- MFA is now standard—patching should be too.
He even joked about printing T-shirts with the slogan, urging organizations to rethink their risk models.
📉 The Rise of “Bad Ransomware”
Not all ransomware is created equal. The newer variants are often poorly coded, meaning victims can’t recover their data—even if they pay.
- Ransomware-as-a-Service (RaaS) is booming.
- Available to even smaller criminal groups.
📡 GPS Jamming, IoT, and Edge Device Vulnerabilities
The session also touched on GPS jamming and IoT threats:
- Devices like cameras and sensors are now powerful enough to launch attacks.
- A single compromised camera in the U.S. led to 400 encrypted servers in Finland.
“Linux is the entry point, but Windows is the chaos engine,” Sami explained.
🧠 AI, Android, and Public Perception
Sami shared why he uses an iPhone instead of Android:
- Android has 28,000+ malware variants daily.
- Public perception matters—especially in cybersecurity.
He also emphasized the importance of educating leadership and changing mindsets, not just systems.
💬 Final Thoughts
This session was a powerful reminder that cybersecurity is no longer just an IT issue—it’s a business survival issue. From ransomware gangs to AI impersonation, the threats are real, organized, and evolving.
“Admin rights are not human rights,” Sami concluded with a smile—and a sticker.